Reading this means you are likely considering whether your organisation should have some aspect of its security tested. Maybe you are researching the topic after clients have asked about it or because some regulation requires it and you would like to know more about what it involves, who performs it, and what to expect from it. This article addresses the most common questions organisations have about penetration testing.
A penetration test is a test of something's security
The term "something" is used here because almost anything can be the subject of such a test. LRQA have tested web, mobile and desktop applications, external networks, internal networks, physical buildings and many other things. If its security is important to your organisation, whether because you have sensitive information to protect or have a product whose reputation is important, then having it tested by an experienced professional is recommended.
The structure of the test can be worked out with the consultancy during a scoping exercise that aligns the test with your business priorities and compliance requirements. For instance, a "pentest" is generally similar to having a planned inspection take place. Think of the consultant as an inspector wearing a brightly colored vest while walking through the estate and noting any observed issues. This kind of test (sometimes referred to as a "grey box" approach when some system knowledge is provided) is generally better for testing an application or network configuration itself and is not meant to be a test of a security appliance (e.g., web application firewall) or the organisation's security team. However, it can be structured to accommodate different testing goals.
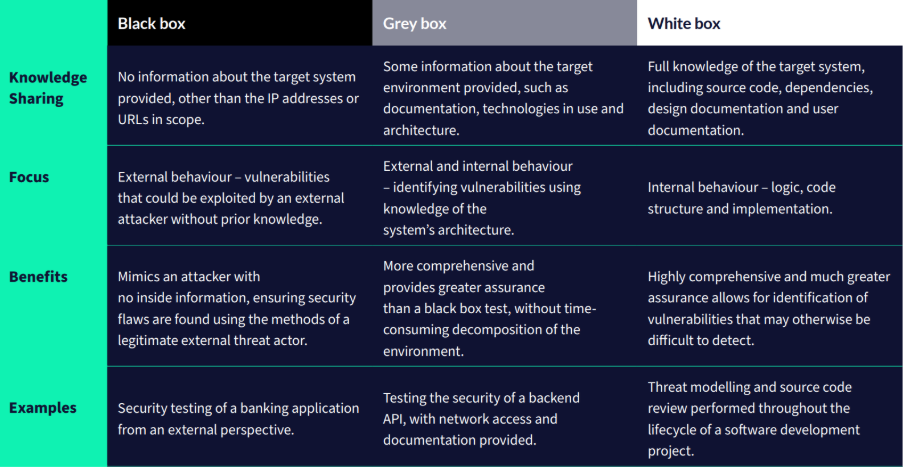
The most extreme configuration is typically called a "red team" engagement. This includes adversary emulation whereby the team of consultants can perform everything from external reconnaissance to social engineering to compromise. They are meant to test the security team and any protections within the estate. In other words, these are the types of tests which involve consultants attempting to remain undetected while bypassing established protections. These types of tests are generally recommended for larger organisations with mature security configurations and teams.
Pentests can generally be flexible in their configuration. For instance, testing a web application with a web application firewall involved is not ideal for testing the application itself since some attacks would likely be stopped by the firewall and provide no information regarding the application itself. However, testing with such protections in place can be done where it meets the client's needs. The key is ensuring the test scope mirrors your real-world risk; too broad and time is wasted on low-value targets; too narrow and attackers will still find paths you never examined.
Testers see things differently
Simply put: the sole focus is on breaking or breaking into things, and usually there is a natural affinity for this kind of thinking. This specialization (and fascination in many cases) leads to viewing applications or infrastructure differently than the teams who build them, which often leads to the discovery of security issues a threat actor may exploit. Such issues could range from simple misconfigurations to insecure implementation of functionality which could put sensitive data, and your organisation's reputation, at risk.
Effective penetration testing goes beyond automated vulnerability scanning by combining manual, context-driven techniques under a predefined scope. While automated tools can highlight surface-level weaknesses, skilled testers trace attack paths end-to-end and translate findings into real business impact (the kind of insight that scanners routinely miss).
To highlight the difference in thinking, consider a web application test where users were prevented from taking certain actions by the application's user interface. In other words, certain input fields were disabled or JavaScript was used to prevent certain fields from being changed. A developer may believe such functionality prevents unanticipated modification of data. However, security experts understand how easily such protections can be bypassed and the result is often unauthorized access to administrator functionality and access to sensitive data.
We seek to give a complete picture of the risk
Though potential solutions to discovered vulnerabilities may be recommended, the focus during testing is on maximizing the impact of a discovered issue and finding alternate routes to sensitive data or vulnerable functionality. This approach mirrors how real attackers chain seemingly minor misconfigurations – an overlooked storage bucket here, a stale user account there – to reach business-critical data. In this way, the final report can explain in detail how seemingly secure aspects of a system can be leveraged to exploit insecure aspects while avoiding detection or previously implemented safeguards.
A real-world example of this comes from a web application which offered solid protection against an attack known as Cross-Site Scripting, whereby malicious code is injected and executed when a target loads the vulnerable page. However, the application allowed users to upload HTML files, among other things, and offered only basic checking for malicious content. This allowed consultants to inject malicious code into an uploaded HTML file and show the ability to compromise administrator accounts with it.
Testers tend to offer a breadth of knowledge
Understanding client concerns allows for your organisation to better serve them. From a security perspective: this requires going beyond how issues with a product can affect the product itself, and understanding how any issues can be leveraged to further attack the client.
Numerous examples of these types of issues can be found by reviewing the list of Common Vulnerabilities and Exposures (CVEs) and other write-ups. While not compromising the application itself, something as simple as default permissions on files created during the installing of an application can be used to elevate privileges on a compromised asset. When found during a penetration test, this type of issue can potentially be resolved before being exploited in "the wild", which may result in reputational harm to your organisation.
Conclusion
An effective penetration test can provide either valuable assurance of a system's security, or valuable information regarding changes needed to improve it, thereby improving client relationships and protecting organisational reputation. With the average data breach costing millions while a focused penetration test represents a fraction of that amount, proactive testing remains an exceptionally cost-effective control – delivering actionable insight, driving remediation, and proving your controls really work against threat actors.
For more detailed information on penetration testing methodologies, compliance requirements, and best practices, refer to the LRQA Essential Guide to Penetration Testing (2025).







